* Il s’agit là peut-être d’une compréhension néfaste et peut-être prémonitoire de l’utilisation de l’image dans le futur.
** J’ai récemment fait ce type de test avec un de mes clients dont la nouvelle charte a été adoptée il y a un an. Pourtant, l’article de présentation de l’entreprise sur Wikipédia utilisait encore l’ancien logo.
http://www.google.com/insidesearch/searchbyimage.html
<title>Search by Image : Getting started – Google Images Help</title>
<meta name= »description » content= »Discover all sorts of content that's related to a specific image. Just specify an image, and you'll find other similar or related images as well as relevant results from across the Web.
http://www.ltutech.com/fr
<meta name= »DC.Title » content= »LTU Technologies | Making sense of visual content » />
<meta name= »description » content= »LTU Technologies provides software for search, retrieval, classification, analysis, recognition and mining of images and videos. The technology is the standard platform for digital forensic analysis in law enforcement and intelligence, including investigations related to child exploitation, intellectual property, brand protection, enterprise search and digital media solutions » />
<meta name= »keywords » content= »accelerated visual analysis,automatic keyword suggestion,accidental or malevolent document leaks,adult content,alexandre winter,amateur bomb plans,analyzing video content,antipiracy,API,artificial vision,assets,authorities,automatic analysis,automatic classification,automatic content recognition of images,autoscan,bank notes,behavior recognition,biometrics,bouncing,brand protection,camera,camouflaged files,CBIR,chahab nastar,child abuse,child exploitation investigations,child exploitation,child porn,child pornography networks,child pornography,child protection,cloned images,clustering,computer forensics,computer vision,content management,content monitoring,copyrighted images,counterfeiting,crawler,crawling,currencies,data flow analysis,data mining,data navigation,defamatory images,digital fingerprint,digital signature,document security,duplicate images,eavesdropping,economic intelligence,encoding,face detection,face recognition,facial analysis,facial recognition,fighting counterfeiting,forensic analysis,GLI,graffitis,gray market,homeland security,human eye,human intelligence,HUMINT,identification,identity cards,identity theft,illegal images,image analysis,image annotation,image categorization,image classification,image correlations,image detection,image DNA,image filter,image filtering,image indexer,image indexing,image keywording,image mining,image processing,image query,image recognition,image retrieval,image retrieving,image search,image searching,image seeker,image segmentation,image shopper,image watcher,image-based investigations,image-guided computer forensics,immersive workspaces,information dominance,INRIA,intellectual property,intelligence agencies,intelligence,internet service providers,internet surveillance,interoperability,investigation,invisible web,IP interception,IST prize,keyword suggestion,keywording,knowledge base,knowledge management,law enforcement,logo search,logos monitoring,look that up,lookthatup,LTU Technologies,LTU,man-machine interfaces,matching,MD5,media monitoring,medialab,messaging systems,metadata,MIT,MMS,mobile photo-phones,monitoring of sensitive images,noburu nakatani,Oxford,passports,patent databases,pattern matching,pedophily,Peer-to-Peer networks,photo album management,photographs,police forces,pornography,prosecution,protection of corporate brands,prototypes,pure visual search,real-time,recognition technology,recognition training,recognizing people,reencoding,representation and visualization of data,retrieval,schemas,SDK,search engine,sebastien gilles,semantic,semi-automatic indexation,sex offenders,SHA1,signal intelligence,similar images,similarity,simulation,SINGINT,speech-to-text,stolen art image mining,stolen art,surveillance of internet,suspicious images,tags,technical diagrams,terrorist threats,text mining,tracking stolen art,trademark search,trademarks misuse,trademarks infringement,traffic in stolen art,traffic of cultural goods,unclassified dataflow,verification,victim identification,video analysis,video editing,video mining,video slicing,video surveillancrus signatures,visible web,visual arts,Visual asset management,visual content,visual data,visual search engine,visual search,visual similarity,visual thesaurus,watermarking,webmining,wiretapping,BIZRATE,ANALYST NOTEBOOK,CORBIS,ENCASE,CYVEILLANCE,EXALEAD,EMAGE,QUAERO,FBI,VECSYS,ICE,INPI,LEGITINAME,NCMEC,OCBC,POLICE,PPR,SWIFTFIND,US customs » />

http://www.tineye.com
<meta name= »title » content= »TinEye Reverse Search Engine » />
<meta name= »description » content= »TinEye is a reverse image search engine built by Idée currently in beta. Give it an image and it will tell you where the image appears on the web. » />
<meta name= »keywords » content= »TinEye, image-based, search engine, visual search, image search, Idee Inc., Idée Inc., Idée Inc. » />
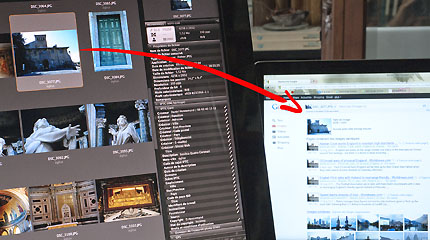
Photo Daniel Hennemand
![]()